Administration tasks consist mostly of incidents, (non)standard changes and monitoring where this blog focusses on monitoring in Office 365. An administrator should proactively monitor the Office 365 environment for alerts and issues. There are a lot of different sources that can trigger an alert where each type of alert should have a process attached to it (there may be additional sources that an administrator should look at, please let me know in a comment or mail and I will update this post). An administrator should for example know who to contact when a DLP alert occurred.
Administration tasks can be categorized in for example daily, weekly and biweekly but this depends on the governance and policy of the organization.
Daily
Daily tasks are mostly tasks that needs to be acted on directly. These are mostly alerts or notifications that are sent to for example a shared mailbox. Processes should be in place to describe the correct way to follow up on the different notifications or alerts.
Service health report
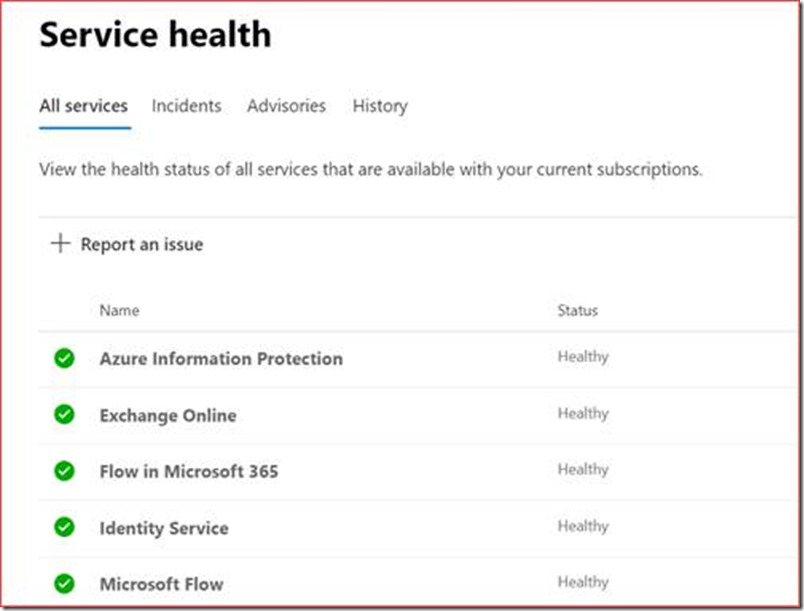
The service health report provided by Microsoft shows incidents and advisories for the different functionalities or products in Office 365. It is possible to build a dashboard in Azure or Power BI that shows this information on a TV screen as you normally won’t notice this until an user reports an issue. The direct link is https://admin.microsoft.com/Adminportal/Home#/servicehealth
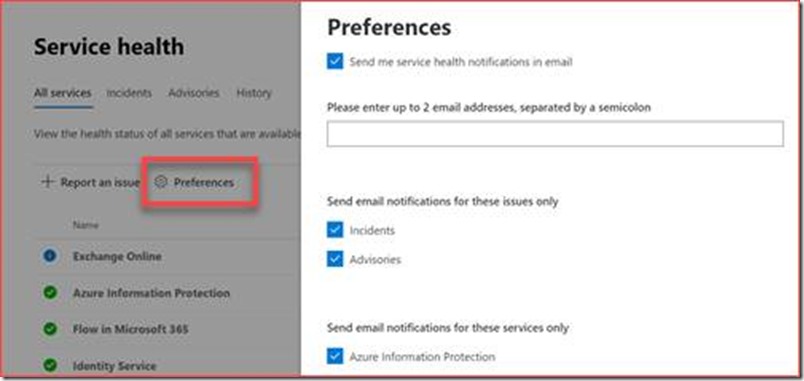
It is currently possible to schedule an alert when you are in the targeted release group. This means you will instantly receive an alert when an incident or advisory has been added. You can schedule this at the same location where you will receive a “Preference” button.
Notifications should be acted on based on a documented process.
Message center
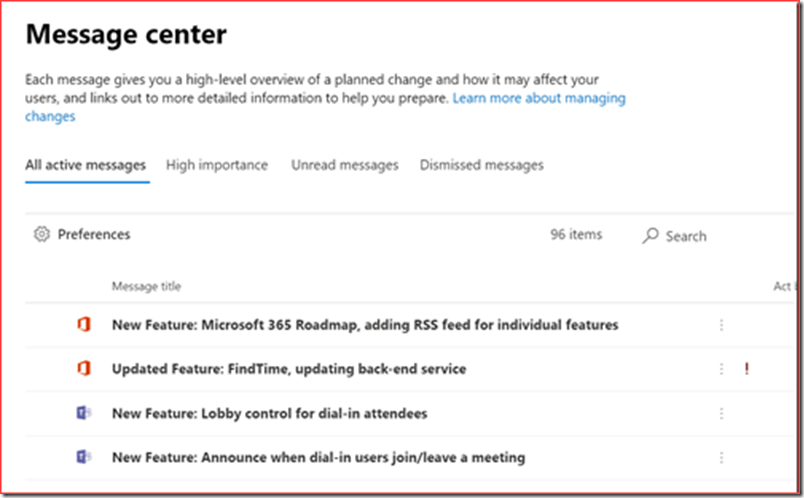
The message center gives you a high-level overview of a planned change and how it may affect your users, and links out to more detailed information to help you prepare. The direct link is https://admin.microsoft.com/Adminportal/Home#/MessageCenter
Messages should be read at least weekly, but it is also possible to schedule notifications with major updates or data privacy messages.
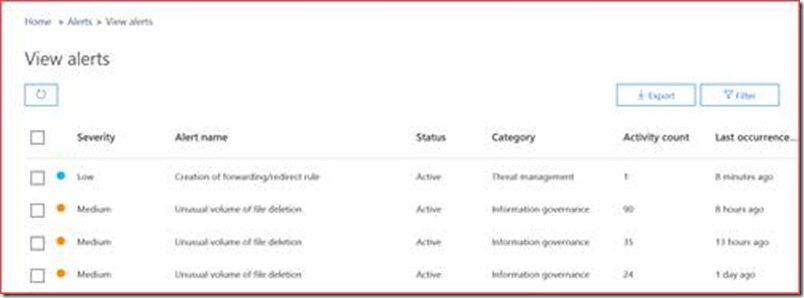
Security & Compliance alerts
It depends on the license what you will see but there is an admin portal for security, an admin portal for compliance and an admin portal for security & compliance. The actual alerts are stored at the security & compliance center with the direct link of https://protection.office.com/viewalerts.
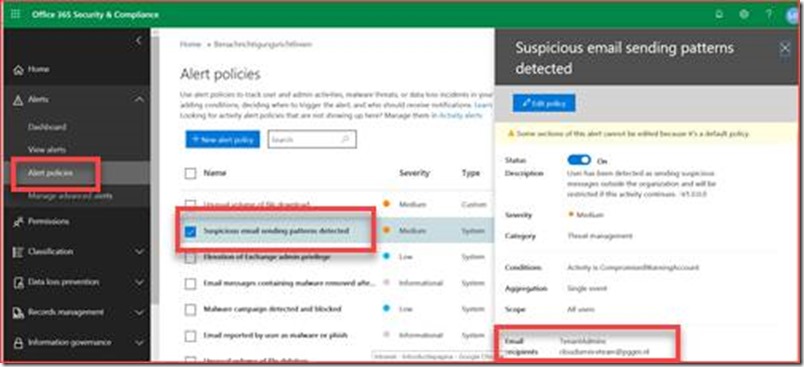
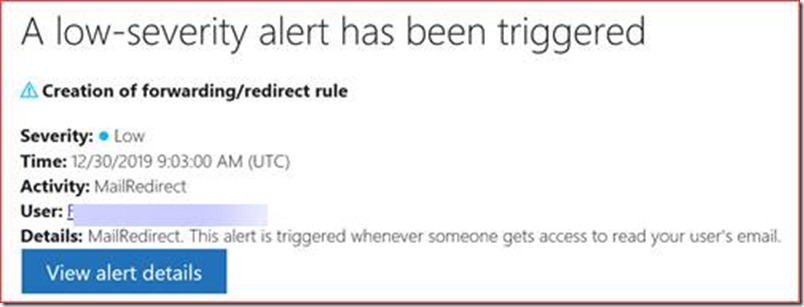
These are alerts of anomalies in for example SharePoint Online and Exchange Online and you can create your own alerts. Each policy will by default be sent to administrators but you can also add a custom mail address by editing each alert policy.
There may be false positives so you will have to tweak the alerts to your preferences, but each alert should be acted on and set to solved in the portal.
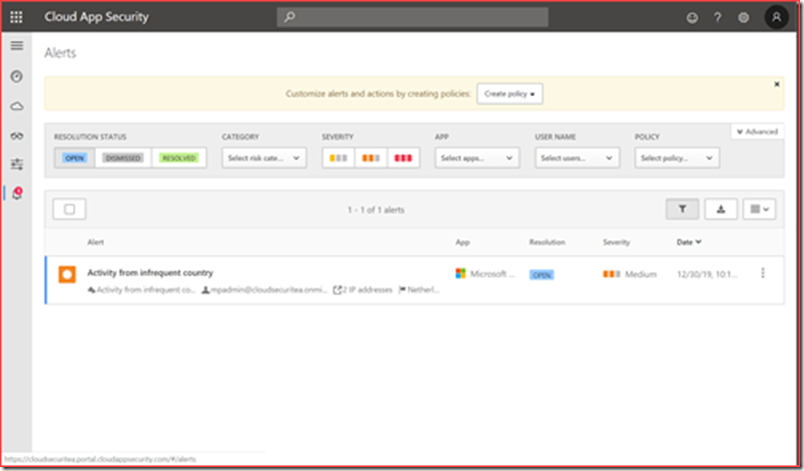
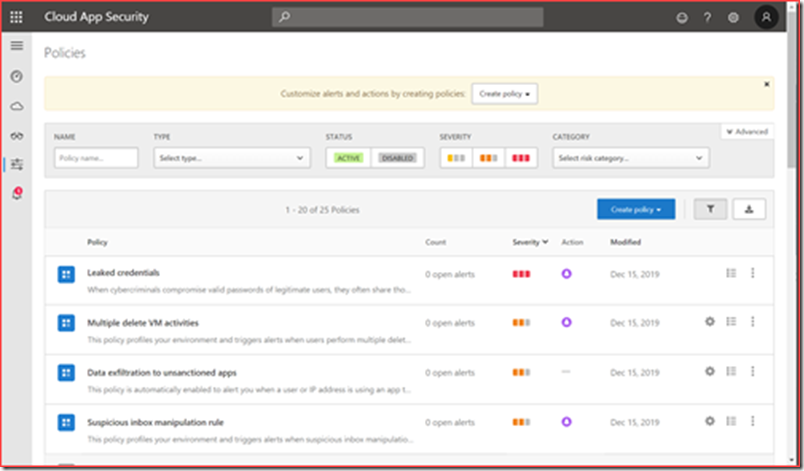
Microsoft Cloud App Security (MCAS) alerts
MCAS is an E5 functionality that uses machine learning and analytical techniques to detect anomalies in your Office 365 tenant. You can find for example login activity from infrequent country or when someone credentials may be leaked.
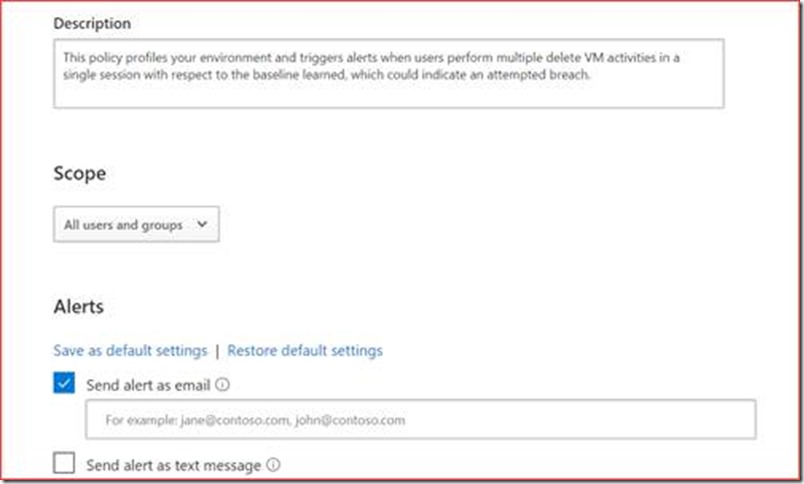
MCAS is build on alert policies where each alert policy should be edited to include a mail address
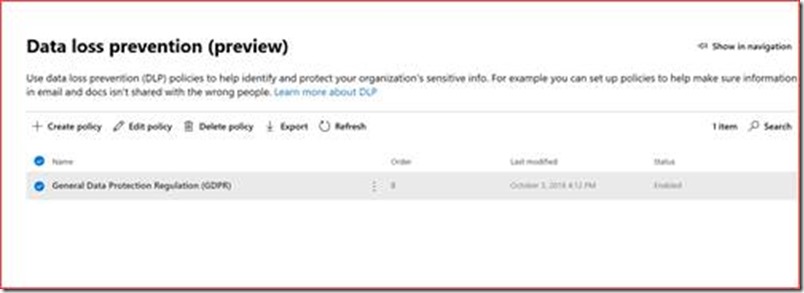
Data loss / leak prevention alerts
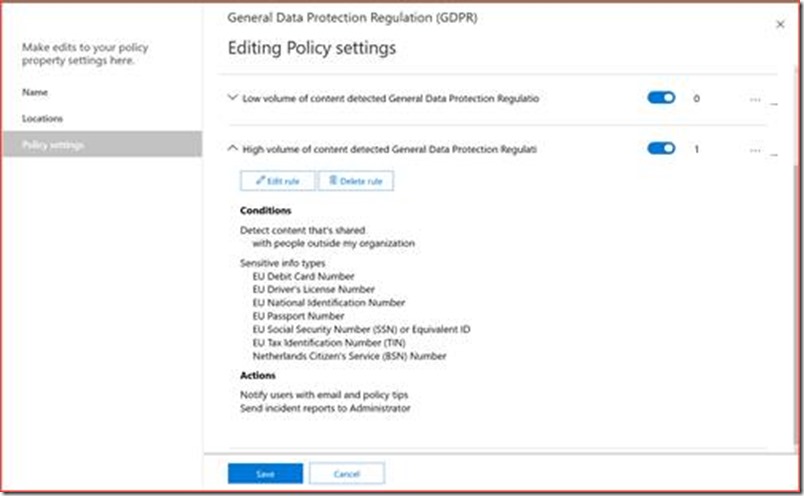
It’s advisable to have at least a PII DLP policy active which helps to be GDPR compliant. DLP alerts show when a user sent data to someone outside your organization that contains for example PII. It depends on the organization and country which PII you should monitor where you can create your own policy. Administrators should monitor these alerts closely and use the correct process so actions can be taken quickly. The direct link is https://compliance.microsoft.com/datalossprevention
You can change the policy to sent a mail to for example a shared mailbox.
Weekly tasks
Message center
The message center gives you a high-level overview of a planned change and how it may affect your users, and links out to more detailed information to help you prepare. The direct link is https://admin.microsoft.com/Adminportal/Home#/MessageCenter
Messages should be read at least weekly and a process should be in place to notify the correct key user when for example something changes in Microsoft Teams.
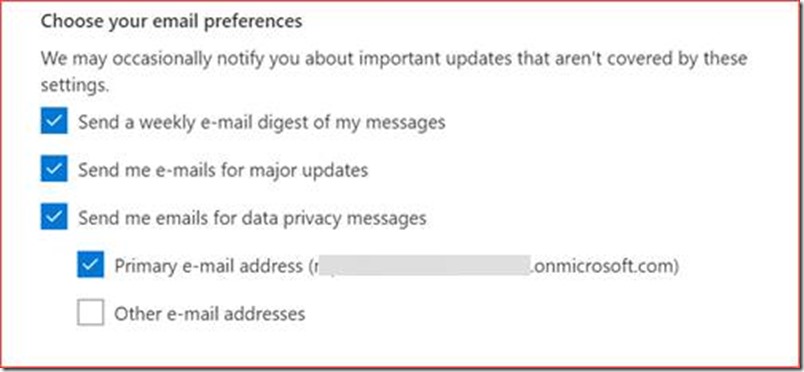
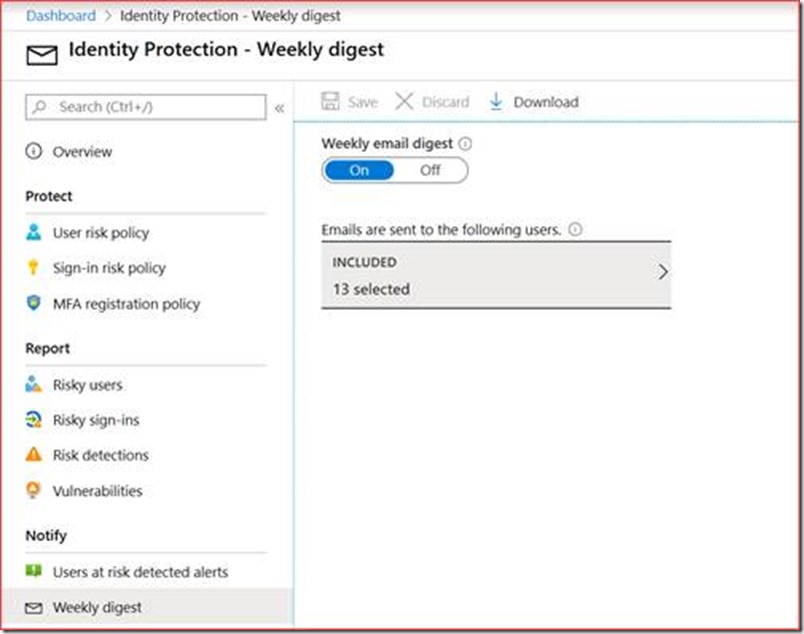
Select ‘Send a weekly e-mail digest of my messages’
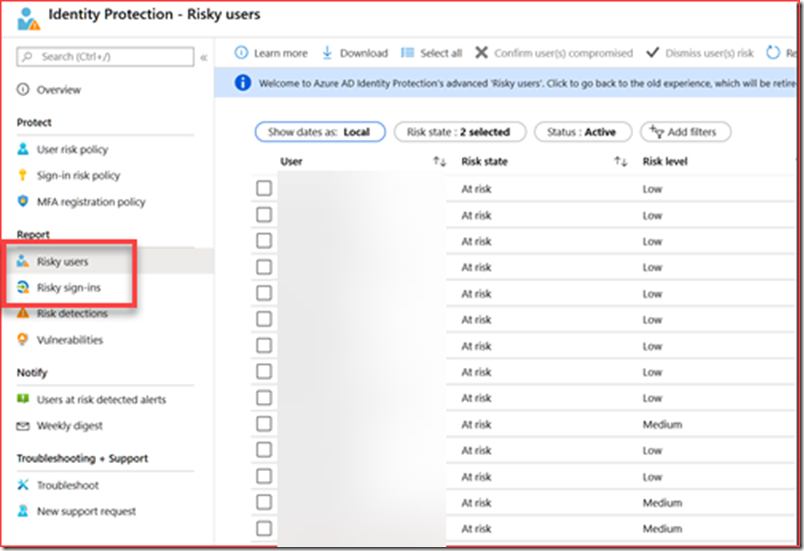
Risky users and risky sign-ins
You should check the alerts for risky users and sign-ins if you have the license. This functionality can be found at the AAD portal https://aad.portal.azure.com
It is advisable to weekly clean up this list so there is no back log. Administrators receive an email by default, but it is possible to add additional users for a weekly mail digest.
Processes should be set in place based on the risk level and type. It is possible to also create actions based on the risk level, but this can increase the incidents for administrators should there be a lot of false positives.
Admin role changes
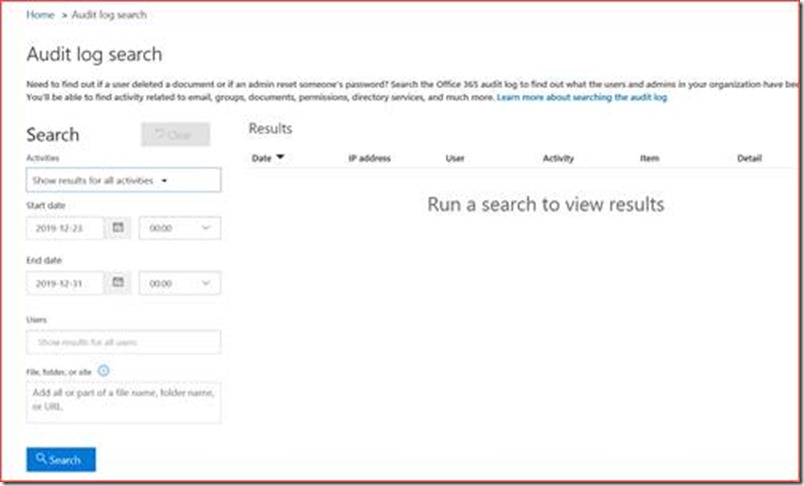
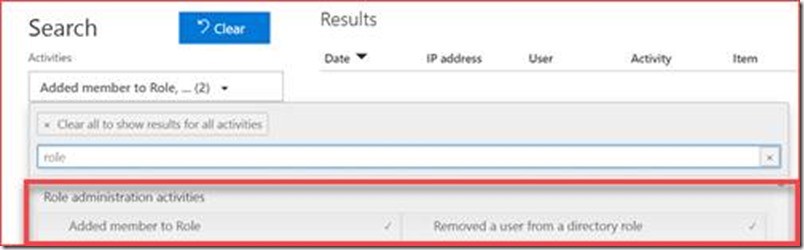
It is best practices to have at least 2 to 4 global administrators in your Office 365 tenant. Each global admin can change roles for users where someone needs to monitor these changes to verify it isn’t being abused. You can verify this using a script, but this will be a snapshot and a global administrator can grant access for 1 hour and then revoke it with only the audit log to prove it in 30 days. The direct link to the audit log is at https://protection.office.com/unifiedauditlog
Search for role administration activities and in particular added and removed members from a role
Security & compliance report
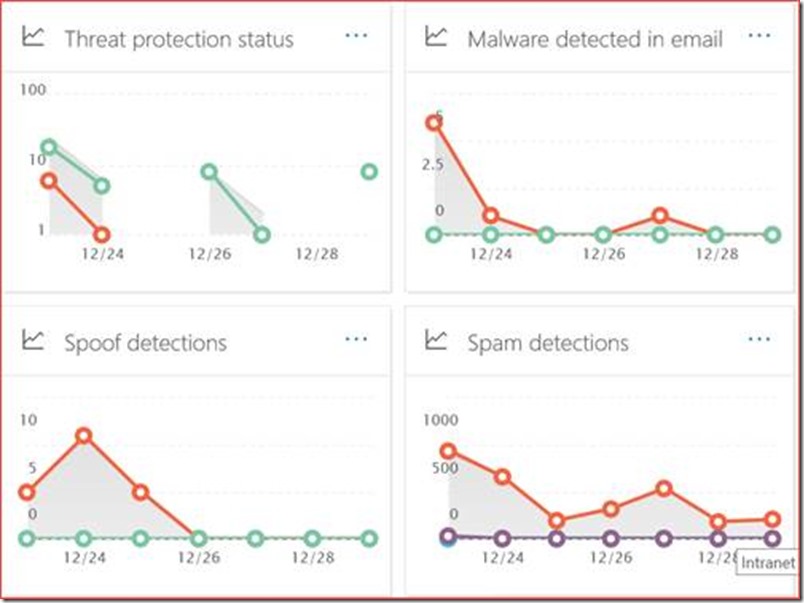
It’s a daily task to verify alerts being produced by the security and compliance center but it’s also advisable to verify the security & compliance dashboard for any differences in spoof, spam or malware detections. The direct link is https://protection.office.com/insightdashboard
Any spikes in the graphs should be looked in to.
New and removed users including licenses
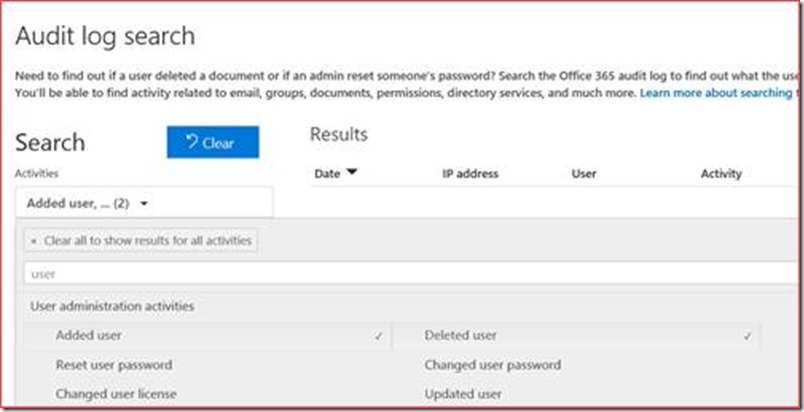
It’s possible that users are being provisioned using a third-party tool, so administrators don’t know how many users are being created weekly or monthly and if there are enough licenses available for these users. You can also verify if strange user accounts have been created during the week. This information is also being retrieved using the audit log at https://protection.office.com/unifiedauditlog
Note that the start and end date is only for a week as it may take some time for the search to complete.
Select at least the added or deleted user.
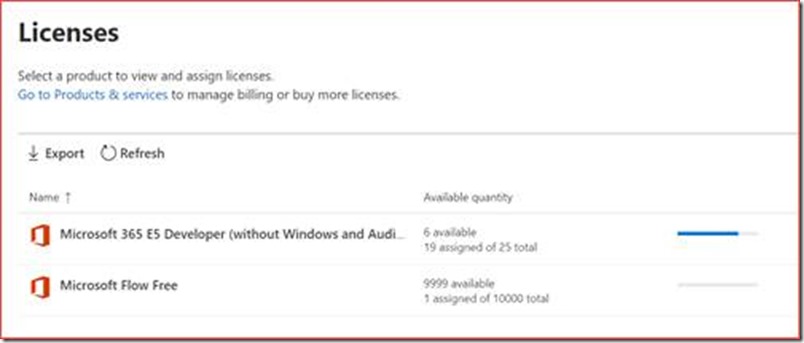
You can also verify at https://admin.microsoft.com/Adminportal/Home#/licenses if there are enough licenses available.
There should be a process in place where the administrator can ask for additional licenses if needed.
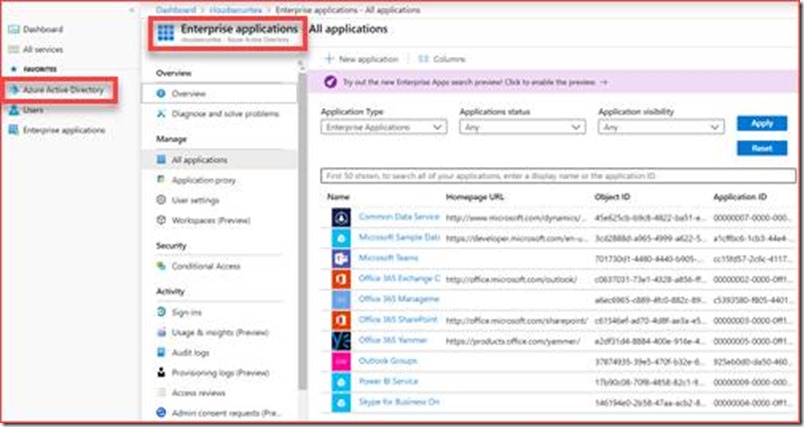
App registrations
We advise to disable app registration to members, but this is enabled by default and should then be monitored closely. A registered app can for example retrieve/use or alter user data and may read the mailbox or sent on behalf of the user. The direct link is https://aad.portal.azure.com/#blade/Microsoft_AAD_IAM/StartboardApplicationsMenuBlade/AllApps/menuId/
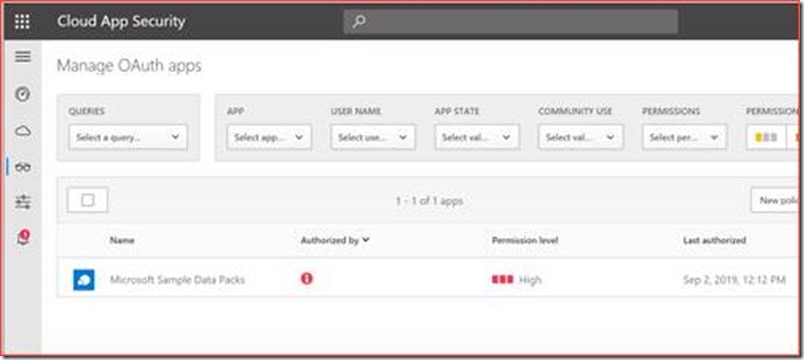
These apps should be verified and removed should they be not allowed in the organization. You can use Microsoft Cloud App Security for a better view of these applications and their risk level.
Note that you will need to connect to your office 365 tenant.
Biweekly tasks
Baseline
I have created a few pages which contain security related settings that can be added to a baseline.
Azure Active Directory
Exchange Online
SharePoint Online
Power Automate and PowerApps
Office 365 Advanced Threat Protection
Office 365 Security & Compliance
Power BI
Microsoft Teams
It is advisable to verify that these settings haven’t been changed in the past two weeks and are still compliant with the baseline. You can use PowerShell or other scripting languages to do this automatically. Any setting that is not compliant should be verified and reverted to the baseline if needed. An investigation can be started to verify who has changed the setting if possible.
![clip_image005[1] clip_image005[1]](https://www.cloudsecuritea.com/wp-content/uploads/2020/01/clip_image0051_thumb.png)
![clip_image007[1] clip_image007[1]](https://www.cloudsecuritea.com/wp-content/uploads/2020/01/clip_image0071_thumb.jpg)
![clip_image026[1] clip_image026[1]](https://www.cloudsecuritea.com/wp-content/uploads/2020/01/clip_image0261_thumb.jpg)