Exchange Online
This page will list security settings and configurations that is advisable to implement in your environment.
Each environment is different where I believe the below settings are easy to setup and provides a way to get to a more mature security level.
- Enforce modern authentication
- Enable common attachment filter
- Restrict access from non compliant devices
- Enable Malware Zero-hour Auto Purge
- Verify SPF records exists
- Verify DMARC records exists
- Verify DKIM records exists and it’s enabled
- Disable calendar sharing with externals
- Client Rules Forwarding Block
- Mailbox Auditing
Enable modern authentication
Modern authentication makes it able to logon using multi-factor authentication, smartcard or using certificates. It is advisable to enforce modern authentication if possible. Multi-factor authentication can be circumvented if basic authentication is still allowed. Should the need arise to allow basic authentication you can also use conditional access to further protect the environment to only allow some users from some locations using basic authentication.
How will this impact my users?
Users will no longer be able to use older or third party applications that only work with basic authentication like Office 2010.
Using PowerShell
You will need to install the Exchange Online module to be able to use the below CMDlets. Run the below CMDlets to enable modern authentication for your Exchange Online environment.
Connect-EXOPSSession
Set-OrganizationConfig -OAuth2ClientProfileEnabled $True
Using conditional access
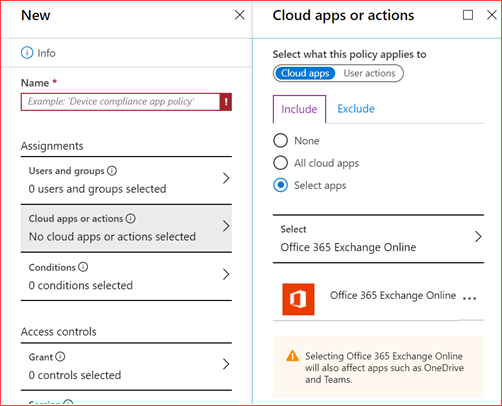
You can use conditional access to block access when basic authentication is used or allow access for basic authentication applications. Click here for the direct link.
Create a new policy and select a group which has all or some of the users. Preferably a dynamic group. And then select for which application this policy applies. In my case I select Exchange Online.
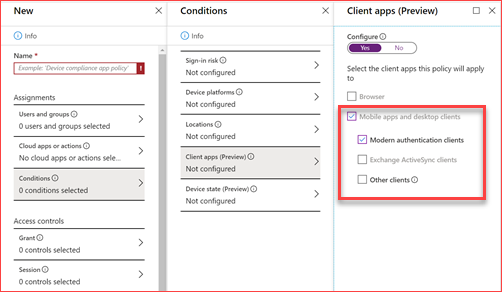
Then under conditionals you can select the authentication client this application can or cannot use. Under Access controls you can block or allow this policy.
Enable common attachment filter
This policy blocks certain file types from being used in mails. You can add or remove file types if needed. It is disabled by default.
How will this impact my users?
Users will no longer be able to send certain file types as attachment.
Using the user interface
You can configure these settings in the Exchange admin portal by going to https://outlook.office365.com/ecp and then Protection -> malware filter
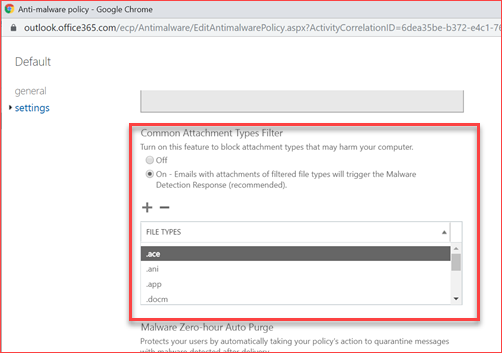
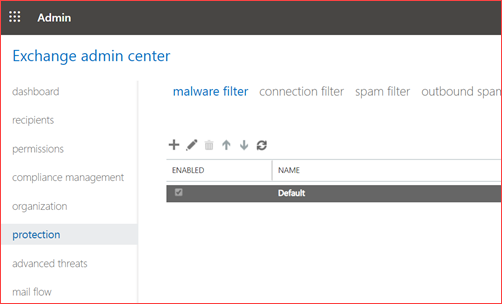 Edit the default filter and enable the common attachment filter
Edit the default filter and enable the common attachment filter
Using PowerShell
You will need to install the Exchange Online module to be able to use the below CMDlets. Run the below CMDlets to enable the common attachment types filter for your Exchange Online environment. You need to specify the correct identity should you have create a custom policy.
Connect-EXOPSSession
Set-MalwareFilterPolicy -Identity Default -EnableFileFilter $true
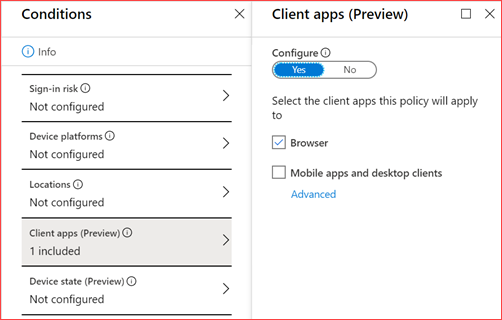
Restrict access from non compliant devices
SharePoint and Exchange Online have the possibility to restrict users from non compliant devices. In Exchange this will restrict users from downloading attachments directly to their system drives. You will need to have Azure Active Directory premium and Intune license as you also need to create a conditional access policy. This is especially helpful to prevent users from downloading documents on devices that are not managed by the company.
How will this impact my users?
Users will no longer be able to download documents from everywhere as it will require a compliant device. When using Intune you can setup your own rules to be sure that content is being secured and managed.
Users have the following experience without the policy when downloading through Outlook Web Access.
Users have the following experience with the policy when downloading through Outlook Web Access.
Using PowerShell
You will need to use PowerShell to change the default Outlook Web App policy. You will also need to install the Exchange Online module to be able to use the below CMDlets. Run the below CMDlets to enable the common attachment types filter for your Exchange Online environment. You need to specify the correct identity should you have create a custom policy. Note that this alone isn’t enough as you will also need to create a conditional access policy.
Connect-EXOPSSession
Set-OwaMailboxPolicy -Identity OwaMailboxPolicy-Default -ConditionalAccessPolicy ReadOnly
Using conditional access
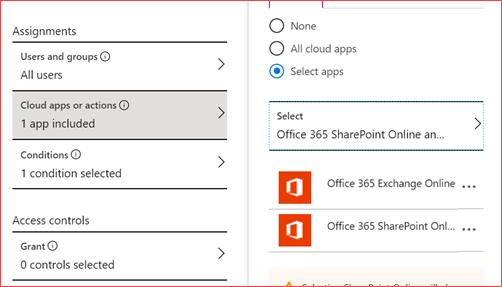
You can customize the SharePoint Online policy should this have been created already or create a new one where you can exclude certain service accounts or want to allow this policy on company devices which are located on-premises. Click here for the direct link.
Make sure you add Exchange Online to this policy
and select that this policy applies to the browser.
and lastly use app enforced restrictions
Enable common attachment filter
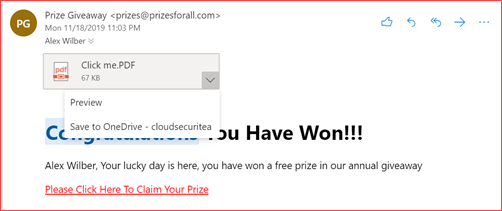
Protects your users by automatically taking your policy’s action to quarantine messages with malware detected after delivery. It is enabled by default but make sure it’s still configured as it is still a new feature at time or writing. You can find more information here.
How will this impact my users?
Mails containing spam, phishing or malware will be automatically removed from users mailboxes. This doesn’t prevent users from clicking on it should the mail still be in the mailbox. It will help for users that didn’t read or acted on the mail yet.
Users will see the following without the policy enabled
 and the following with the policy
and the following with the policy
Using the user interface
You can configure these settings in the Exchange admin portal by going to https://outlook.office365.com/ecp and then Protection -> malware filter
 Ensure the Malware Zero-hour Auto Purge is On and we suggest you add a mail address for notications.
Ensure the Malware Zero-hour Auto Purge is On and we suggest you add a mail address for notications.
Using PowerShell
You will need to install the Exchange Online module to be able to use the below CMDlets. Run the below CMDlets to enable the common attachment types filter for your Exchange Online environment. You need to specify the correct identity should you have create a custom policy.
Connect-EXOPSSession
Set-MalwareFilterPolicy -Identity Default -ZapEnabled $true
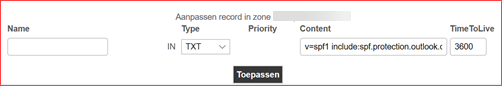
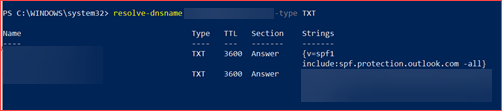
Verify SPF records exists
A Sender Policy Framework (SPF) record should be created for each domain. An SPF record tells Exchange Online who else can mail via this server. You can for example add an internal SMTP IP or FQDN so this can use the Exchange Online server. SPF records prevents for example spoofing. The default value you should add is v=spf1 include:spf.protection.outlook.com -all where you may add additional IP’s or FQDN’s. Note that you need to update the SPF-record each time a third party or internal IP or FQDN is removed. Click here for more information.
How will this impact my users?
This setting has no impact on users but applications aren’t able to relay messages if the SPF record is not correct.
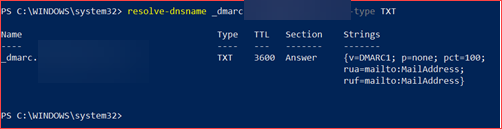
Verify DMARC records exists
A Domain-Based Message Authentication, Reporting and Conformance (DMARC) record should be created for each maildomain. Below a quote from Microsoft which can be found here:
Domain-based Message Authentication, Reporting, and Conformance (DMARC) works with Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) to authenticate mail senders and ensure that destination email systems trust messages sent from your domain. Implementing DMARC with SPF and DKIM provides additional protection against spoofing and phishing email. DMARC helps receiving mail systems determine what to do with messages sent from your domain that fail SPF or DKIM checks.
How will this impact my users?
This setting has no impact on users.
Using the user interface
You will need to add this record to each domains DNS list. The DNS list can be altered at your domain providers website. Add a TXT-record with the value “_dmarc” which should translate to _dmarc.<Domain>.<Extension> and add as content “v=DMARC1; p=none; pct=100; rua=mailto:<MailAddress>; ruf=mailto:<MailAddress>; fo=1
Verify DKIM records exists and it’s enabled
DomainKeys Identified Mail (DKIM) records should be created for each domain. DKIM with SPF and DMARC will prevent spoofers from tying to spoof the domain. It allows for non-repudation as the receiver can verify that the sender is correct.
How will this impact my users?
This setting has no impact on users.
Using the user interface
There are two things you need to do to enable DKIM.
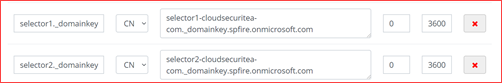
- DNS Records
You will need to add the below records to each domains DNS list. The DNS list can be altered at your domain providers website. Add the below CNAME records
Host name: selector1._domainkey
Points to address or value: selector1-<DomainName>-<Extension>._domainkey.<TenantName>.onmicrosoft.com
TTL: 3600
Host name: selector2._domainkey
Points to address or value: selector2-<DomainName>-<Extension>._domainkey.<TenantName>.onmicrosoft.com
TTL: 3600
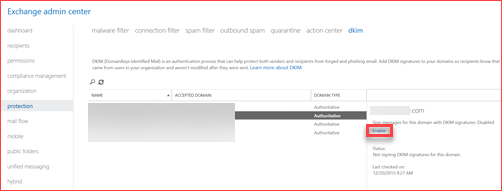
- Exchange Admin Portal
Go to protection -> Dkim and click on Enable after you updated the DNS records.
Using PowerShell
You can enable DKIM with the below PowerShell command after you created/updated the DNS records.
Set-DkimSigningConfig -Identity -Enabled $True
Disable calendar sharing with externals
Attackers can retrieve a lot of information from calendars which are available outside the organizations. Preventing calendar sharing will limit the possibility for attackers to analyze your behavior or the kind of meetings your employees have.
How will this impact my users?
Users will not be able to share their calendar with external users. They can still share it with colleagues.
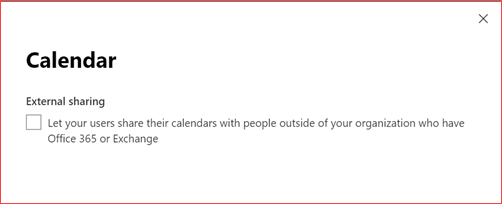
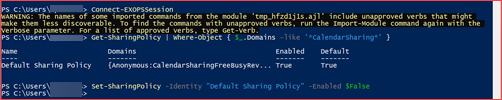
Using the user interface
You can change this setting using the default admin portal of Office 365 at https://admin.microsoft.com. Navigate to Settings -> Settings -> Calendar
 Make sure you deselect the checkbox to disable sharing with external users
Make sure you deselect the checkbox to disable sharing with external users
Using PowerShell
You can change this setting using PowerShell. The below Cmdlet can be used to change this setting. You will need the Exchange Online PowerShell module for this. You may need to change the name of the identity if you created a custom policy.
Connect-EXOPSSession
Set-SharingPolicy -Identity “Default Sharing Policy” -Enabled $False
Client Rules Forwarding Block
You should create the Client Rules Forwarding Block transport rule to disable users from auto forwarding emails to external domains. This is to prevent users from directly sending emails to other mail addresses but it also prevents attackers who have access to a mailbox to configure which may configure a auto forward rule.
How will this impact my users?
Users can’t auto forward mail from their mailbox directly to for example their Live account.
Using the user interface
You can add this rule using the Exchange Admin portal at https://outlook.office.com/ecp/.
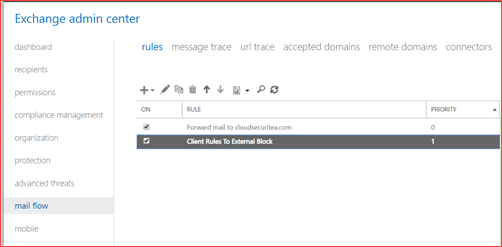 Create a new rule where I already added one
Create a new rule where I already added one
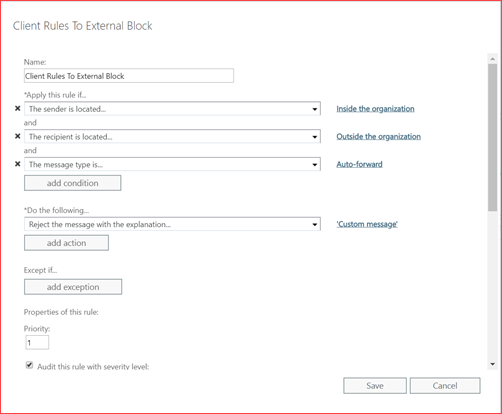 Configure the rule to block mails from inside the organization to outside the organization.
Configure the rule to block mails from inside the organization to outside the organization.
Using PowerShell
You can add this rule using PowerShell. The below Cmdlet can be used to add the rule. You will need the Exchange Online PowerShell module for this. You can customize the text.
Connect-EXOPSSession
$MessageText = “Custom text for the user”
New-TransportRule -name “Client Rules To External Block” -Priority 1 -SentToScope NotInOrganization -FromScope InOrganization -MessageTypeMatches AutoForward -RejectMessageEnhancedStatusCode 5.7.1 -RejectMessageReasonText $MessageText
Mailbox Auditing
Mailbox auditing enables administrators to track logons and activities related to mailboxes using the audit log. It may be required to enable mailbox auditing due to compliance policies or you can enable it for forensics. Administrators aren’t able to read the mail but they can help the user if issues occur with the mailbox. This setting is enabled by default since January 2019 but it’s advisable to verify if all mailbox have auditing enabled.
How will this impact my users?
There is no user impact.
Using the user interface
There is no option to verify which mailboxes have auditing enabled via the Exchange admin portal. You will need to use PowerShell.
Using PowerShell
You will need the Exchange Online PowerShell module for this. Using the below Cmdlet you can verify which mailbox doesn’t have auditing enabled
Connect-EXOPSSession
Get-Mailbox -ResultSize Unlimited | Where-Object {$_.AuditEnabled -eq $False} | Format-Table Name, AuditEnabled
You can then enable auditing using the below Cmdlets
Get-Mailbox -ResultSize Unlimited | Where-Object {$_.AuditEnabled -eq $False} | Set-Mailbox -AuditEnabled $true -AuditOwner MailboxLogin,HardDelete,SoftDelete,Update,Move -AuditDelegate SendOnBehalf,MoveToDeletedItems,Move -AuditAdmin Copy,MessageBind