Azure Active Directory
This page will list security settings and configurations that is advisable to implement in your environment.
Each environment is different where I believe the below settings are easy to setup and provides a way to get to a more mature security level.
Multi-factor authentication for all admins
There are a lot of admin roles a user can receive. Some admin roles are restrictive in what the user is able to do but for example global/SharePoint and Exchange administrators can change a lot of settings where you want an additional layer of authentication before they can log on. You have a single point of failure when not using multi-factor authentication. The username and password is enough to log on to a users mailbox or OneDrive folder. Fishing mails are mostly used to retrieve the users username and password where the attacker can then easily log on with these credentials. Multi-factor authentication makes it difficult for the attacker to log on as they will also need to have your phone where for example an SMS token is being sent. Although the attacker may steal your credentials, they are not able to get access to your information. Note that a lot of sites and applications offer multi-factor authentication, its normally not enabled by default.
How will this impact my users?
Users will receive a notice the next time they log on saying they will need to configure the authenticator app or SMS/phone by adding the phone number. You can limit the options for the user to only allow the authenticator app. It is possible to allow users to remember the multi-factor authentication on devices they trust so they won’t need to authenticate using multi-factor authentication each time.
Using the user interface
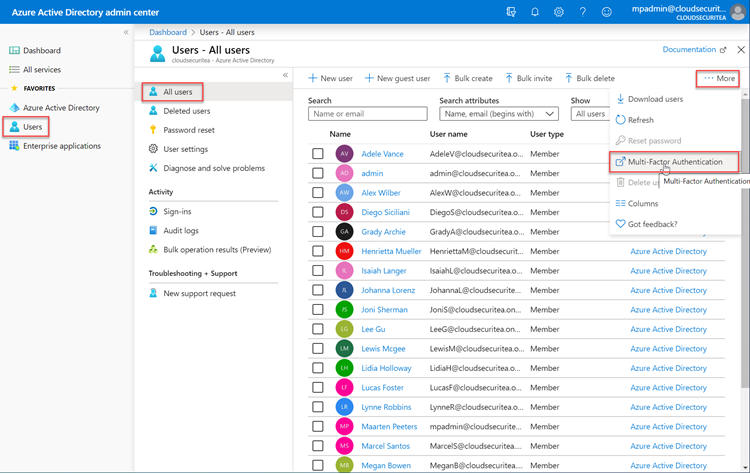
You can enable multi-factor authentication manually per user by going to https://aad.portal.azure.com -> Users -> All users -> … More -> Multi-Factor Authentication
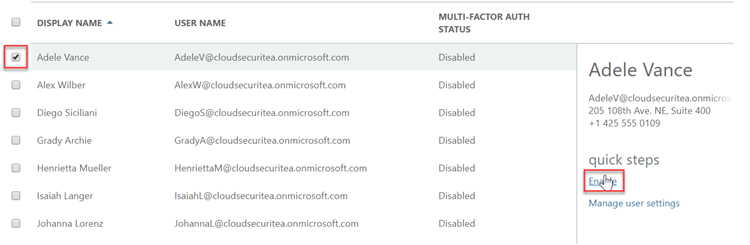
Then you can select the user and click on ‘Enable’
Using conditional access
You can use conditional access to force multi-factor authentication for administrators but you will need to have the Azure Active Directory Premium plan 1 license. Click here for the direct link.
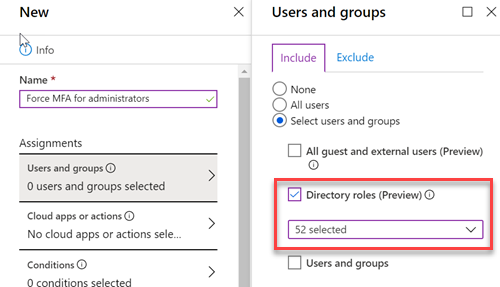
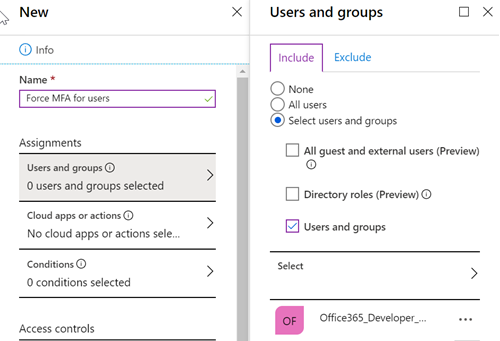
Create a new policy and select all directory roles under users and groups
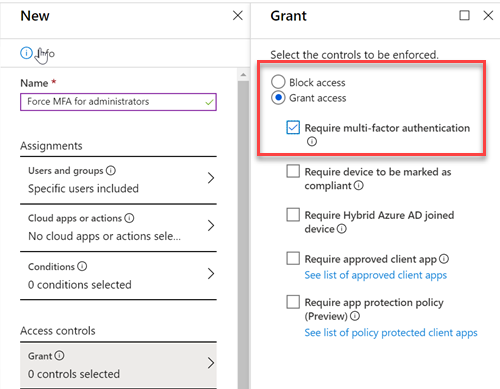
Then select require multi-factor authentication and save the policy
Using PowerShell
You will need to install the MSOnline module to be able to use the below CMDlets. Run the below CMDlets to enable multi-factor authentication for all administrators.
$mf= New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationRequirement
$mf.RelyingParty = “*”
$mfa = @($mf)
Get-MsolRole | ForEach-Object { Get-MsolRoleMember -RoleObjectId $_.ObjectId } | Where-Object {-NOT $_.StrongAuthenticationRequirements.state} | Set-MsolUser -userprincipalname $_.UserPrincipalName -StrongAuthenticationRequirements $mfa
Multi-factor authentication for all users
It is just as important to enable multi-factor authentication for users as it is for administrators. Administrators have the ability to manage the environment but the users hold the data in their mailbox or in OneDrive. You will want to enable multi-factor authentication also for them. You have a single point of failure when not using multi-factor authentication. The username and password is enough to log on to a users mailbox or OneDrive folder. Fishing mails are mostly used to retrieve the users username and password where the attacker can then easily log on with these credentials. Multi-factor authentication makes it difficult for the attacker to log on as they will also need to have your phone where for example an SMS token is being sent. Although the attacker may steal your credentials, they are not able to get access to your information. Note that a lot of sites and applications offer multi-factor authentication, its normally not enabled by default.
How will this impact my users?
Users will receive a notice the next time they log on saying they will need to configure the authenticator app or SMS/phone by adding the phone number. You can limit the options for the user to only allow the authenticator app. It is possible to allow users to remember the multi-factor authentication on devices they trust so they won’t need to authenticate using multi-factor authentication each time.
Using the user interface
You can enable multi-factor authentication manually per user by going to https://aad.portal.azure.com -> Users -> All users -> … More -> Multi-Factor Authentication
Then you can select the user and click on ‘Enable’
Using conditional access
You can use conditional access to force multi-factor authentication for administrators but you will need to have the Azure Active Directory Premium plan 1 license. Click here for the direct link.
Create a new policy and select a group which has all the users. Preferably a dynamic group. In my case I use the same group I use for group based licensing as these are the users who have an active license to Office 365. A different conditional access policy restricts users without a license to log on to the environment.
Then select require multi-factor authentication and save the policy
Using PowerShell
You will need to install the MSOnline module to be able to use the below CMDlets. Run the below CMDlets to enable multi-factor authentication for all administrators.
$mf= New-Object -TypeName Microsoft.Online.Administration.StrongAuthenticationRequirement
$mf.RelyingParty = “*”
$mfa = @($mf)
Get-MsolUser -All | Where-Object {-NOT $_.StrongAuthenticationRequirements.state -and $_.isLicensed -eq $true} | Set-MsolUser -userprincipalname $_.UserPrincipalName -StrongAuthenticationRequirements $mfa
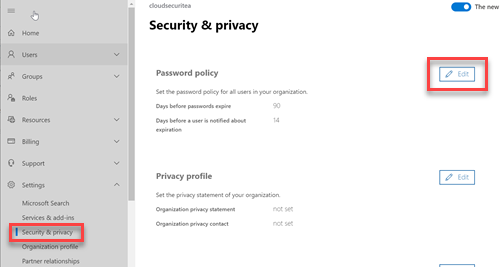
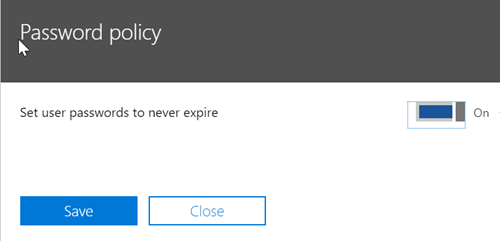
Password expiration to never expire
Users need to remember a lot of passwords, not only at work but also for other websites. You want to prevent users from writing down their passwords in a book that is next to the computer or using post-its sticked to the computer itself with their password. The need for a recycling of passwords is less when you implement multi-factor authentication as the password alone isn’t enough to get access to the account. You will still need to reset the password should there be signs of malicious activity for that user but forcing the user to create a new password every 3 months isn’t the way to go. The user will create simpler passwords to remember them as variations of the current password is most of the time not allowed. NIST also references this in NIST SP 800-63 https://pages.nist.gov/800-63-FAQ/#q-b05
How will this impact my users?
Users will no longer receive the message to create a new password after expiration.
Using PowerShell
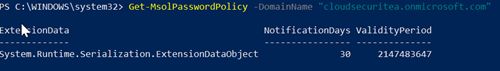
You will need to install the MSOnline module to be able to use the below CMDlets. Run the below CMDlets to set the password expiration to never for all domains.
get-msoldomain | ForEach-Object {Set-MsolPasswordPolicy -ValidityPeriod 2147483647 -DomainName $_.Name -NotificationDays 30}
Two to four global administrators
Global administrators have full permissions in Office 365 where you want to limit the amount of administrators with these permissions. It is also good to have at least two global administrators should the other administrator go on vacation. Administrators should receive the least amount of privilege to be able to do their day-to-day work. Exchange administrators should receive the Exchange admin role and the same for SharePoint or Team administrators. We also suggest to limit the amount of administrators for other admin roles as it is normally not required for more then 4 users to be a SharePoint administrator.
How will this impact my users?
Administrators will loose permissions to change other components with a more restrictive role. Be sure to grant administrators enough permissions so they will be able to do their work correctly.
Using the user interface
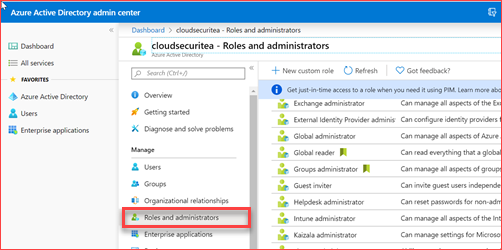
You can verify the amount of users assigned to a role in the Azure Active Directory Portal by going to Azure Active Directory -> Roles and administrators and then select the role you want to verify.
This can be a lot of work to verify 50+ roles so we suggest to user PowerShell to verify that should a role have users assigned, that there are at least 2 and a maximum of 4.
Using PowerShell
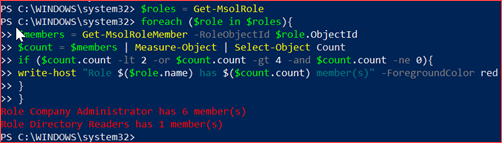
You will need to install the MSOnline module to be able to use the below CMDlets. Run the below CMDlets to verify the amount of administrators for each role.
$roles = Get-MsolRole
foreach ($role in $roles){
$members = Get-MsolRoleMember -RoleObjectId $role.ObjectId
$count = $members | Measure-Object | Select-Object Count
if ($count.count -lt 2 -or $count.count -gt 4 -and $count.count -ne 0){
write-host “Role $($role.name) has $($count.count) member(s)” -ForegroundColor red
}
}
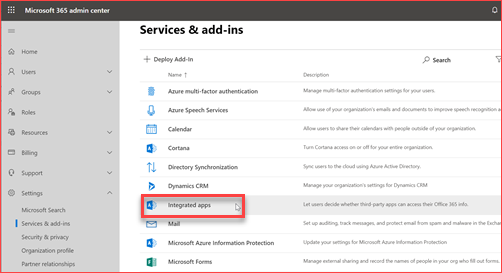
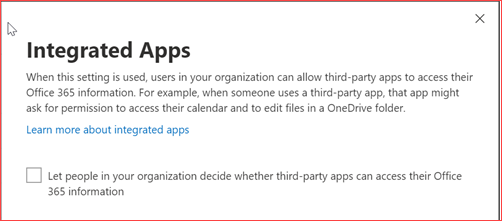
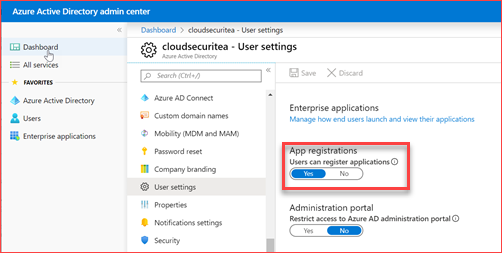
Restrict users to grant consent to unmanaged applications
Users are by default able to grant consent to third party applications. They are for example able to logon to LinkedIn or Kahoot with their credentials. The third party application will then ask for consent where the user can grant it for themselves. It is advisable to block users from being able to give consent for these applications as they should be managed. It is possible for administrators to grant consent where all users or a group of users can then use this application. Most of the third party application won’t require much permissions but there are third party applications that wants read and write access to for example the users mailbox. Note that previous added apps will continue to work for the users that granted consent. There isn’t a good PowerShell CMDlet yet so I will use the GUI where this setting needs to be applied on two places.
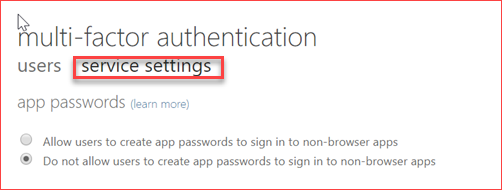
Disable app passwords
An app password can be used when a third party application doesn’t support multi-factor authentication. It is then possible to log on to the application using an app password. The issue with app passwords is that it bypasses conditional access where you may have a policy to only allow compliant devices from authenticating to Azure Active Directory. An app password can be used to authenticate where the conditional access policy isn’t being forced.
How will this impact my users?
Users can no longer use third party applications who doesn’t support multi-factor or modern authentication.
Enable self service password reset
It is not really a security feature but enabling self service password reset will help administrators. Users can now reset there own password which means they don’t need to fill in a ticket. It’s free for cloud users where synced users will need an Azure Active Directory premium license.
In Azure Active Directory Portal.
Click here for the direct link or go to Azure Active Directory -> Password reset
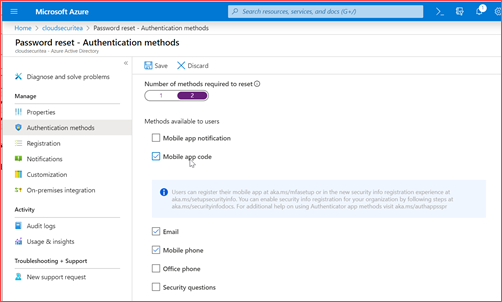
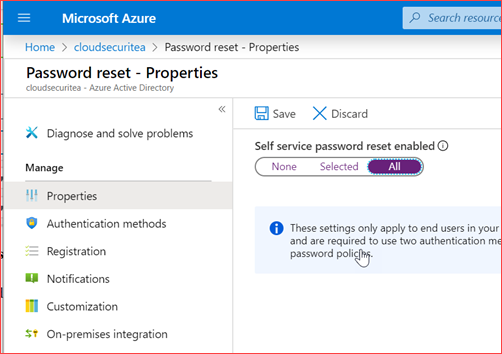 You can set the policy for all users or a select few users. It is also advisable to set 2 number of methods required to reset the password.
You can set the policy for all users or a select few users. It is also advisable to set 2 number of methods required to reset the password.
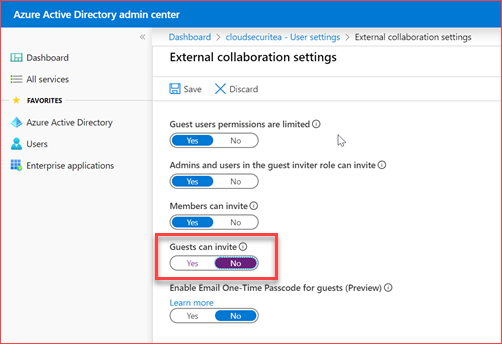
Disable guests can invite
There are a few collaboration settings which needs to be looked in to. Each organization has their own requirements where you can set who can invite guests to the Azure Active Directory. You can only allow administrators or users with the guest invite role to invite guests or you can allow members to invite guests. We advice you disable the option to allow guests to invite guests. Note that this option is currently enabled by default.
How will this impact my users?
It depends on the configuration but there is no user impact if you only disable the option to let guests invite other guests.
Using the user interface
Click here to go directory to the settings location or go to the Azure Active Directory -> User Settings -> Manage external collaboration settings