Office 365 Advanced Threat Protection
This page will list security settings and configurations that is advisable to implement in your environment.
Each environment is different where I believe the below settings are easy to setup and provides a way to get to a more mature security level.
ATP Safe Attachments
Safe Attachments is a next level anti-malware solution where all mail attachments will be routed through Microsoft. Microsoft verifies all attachments using machine learning and analysis techniques by for example detonating this in a sandbox. Microsoft collects information from all tenants and Live.com and used this near real-time for Office 365. Your tenant in the United States is protected from malware should the same attachment already been scanned in the Netherlands.
Note that ATP Safe Attachments also works for SharePoint, OneDrive, and Microsoft Teams
How will this impact my users?
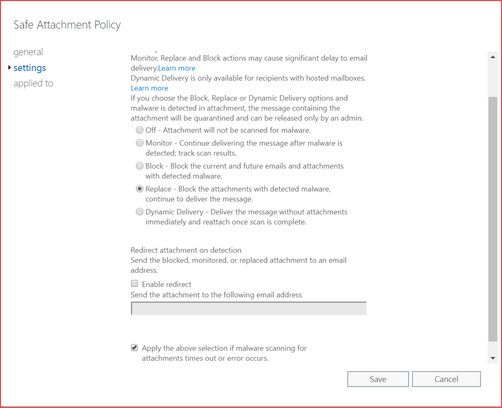
The administrator can decide the user impact where you have the following options:
- Monitor – Continue delivering the message after malware is detected; track scan results.
- Block – Block the current and future emails and attachments with detected malware.
- Replace – Block the attachments with detected malware, continue to deliver the message.
- Dynamic Delivery – Deliver the message without attachments immediately and reattach once scan is complete.
We suggest selecting replace as it will raise more questions from users should they receive mails without attachments. The behavior is also currently that should the mail be read it will be marked as unread again after the attachment has been added. Users will receive an e-mail delay when selecting any option.
Using the user interface
You can go to directly to https://protection.office.com/threatpolicy
Click on ATP safe attachments
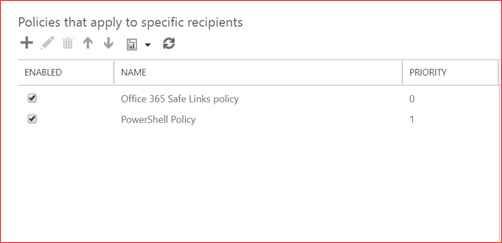
Enable ATP for SharePoint, OneDrive and Microsoft Teams. Add or edit the current policy
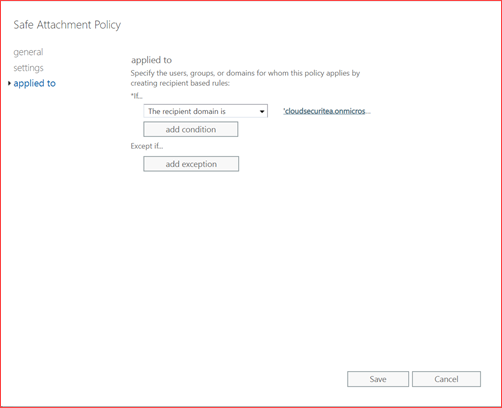
Select your preference and set a redirect mail as you may need the attachment for analysis but make sure you open this in a sandbox environment.
Add the recipient domain to enable this for these users.
Using PowerShell
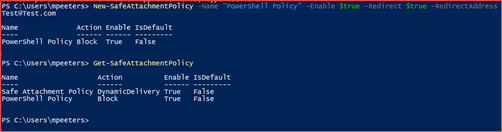
You can use PowerShell to automatically set a policy. You can use the new Exchange Online module.
Connect-EXOPSSession
New-SafeAttachmentPolicy -Name “PowerShell Policy” -Enable $true -Redirect $true -RedirectAddress Test@Test.com
New-SafeAttachmentRule “PowerShell Policy” -RecipientDomainIs “cloudsecuritea.onmicrosoft.com” -SafeAttachmentPolicy “PowerShell Policy” -Enabled $true
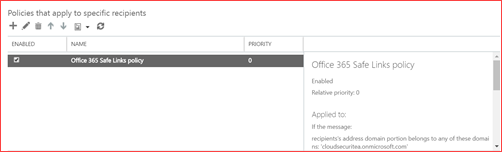
ATP Safe Links
Safe Links is a next level anti-phishing solution where each link you click on in Office 365 or Office will be protected by using time-of-click verification. The link will be verified using analysis techniques and machine learning and some links will be detonated in a sandbox. ATP Safe Links also verifies all links being sent in the mail after this policy has been setup. This prevents the mail from reaching the user. Each URL is being wrapped by Microsoft and the user will be redirected via Microsoft to the correct destination.
Note that ATP Safe Attachments also works for SharePoint, OneDrive, Office and Microsoft Teams
How will this impact my users?
The administrator can decide the user impact where you have the following options:
- Hold – Sent the email after scanning has been completed
- Deliver – Sent the email directly and remove it should the scan identify phishing.
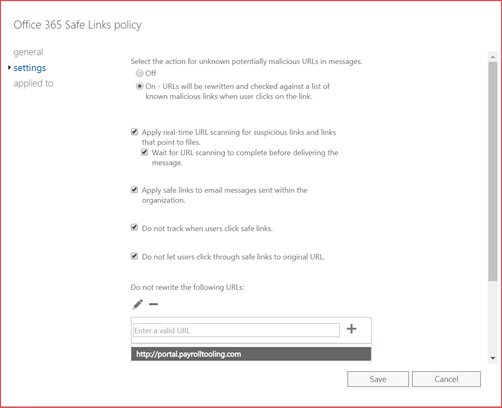
We suggest selecting hold as it will raise more questions from users should they receive mails with phishing included. Users will receive an e-mail delay when selecting the hold option. Links will be wrapped so users will see something like https://eur03.safelinks.protection.outlook.com with a lot of parameters.
Note that you can select to track the URL’s which users click on but inform your employees before activating this feature as it will track their behavior.
Using the user interface
You can go to directly to https://protection.office.com/threatpolicy
Click on ATP safe links and first edit the default rule.
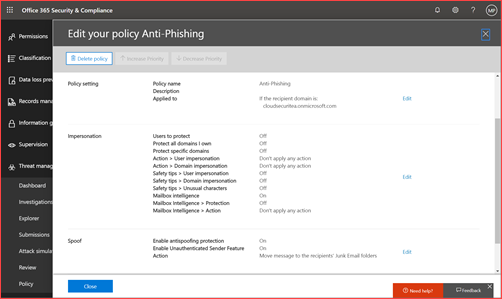
Add or edit a created policy
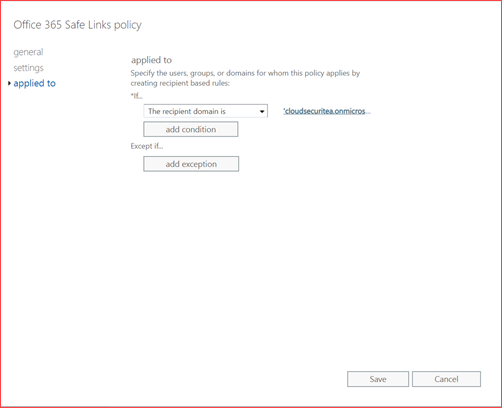
Select the settings you prefer and go to applied to.
Select the domain for whom this policy applies.
Using PowerShell
You can use PowerShell to automatically set a policy. You can use the new Exchange Online module.
Connect-EXOPSSession
New-SafeLinksPolicy “PowerShell Policy” -TrackClicks $false -IsEnabled $true -AllowClickThrough $false
New-SafeLinksRule “PowerShell Policy” -SafeLinksPolicy “PowerShell Policy” -RecipientDomainIs “cloudsecuritea.onmicrosoft.com” -Enabled $true
ATP Anti-Phishing
By default, Office 365 includes built-in features that help protect your users from phishing attacks. Set up anti-phishing polices to increase this protection, for example by refining settings to better detect and prevent impersonation and spoofing attacks. You can finetune and set a stricter policy for some users.
How will this impact my users?
Users will be better protected from phishing where these mails will be removed or sent to the junk folder. There may be false positives so it’s advisable to implement a procedure to whitelist domains.
Using the user interface
You can go to directly to https://protection.office.com/threatpolicy
Click on ATP anti-phishing
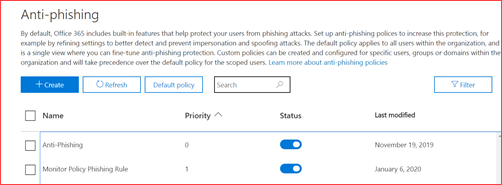
Add or edit a created policy
Set the policy based on your organization preferences
Using PowerShell
You can use PowerShell to automatically set a policy. You can use the new Exchange Online module.
Connect-EXOPSSession
New-AntiPhishPolicy -Name “Monitor Policy” -AdminDisplayName “Default monitoring policy” -Enabled $true -EnableOrganizationDomainsProtection $true -EnableTargetedDomainsProtection $true -TargetedDomainsToProtect fabrikam.com -TargetedUsersToProtect “Adele Vance;AdeleV@cloudsecuritea.onmicrosoft.com” -EnableMailboxIntelligence $true -EnableSimilarUsersSafetyTips $false -EnableSimilarDomainsSafetyTips $false -TargetedDomainProtectionAction BccMessage -TargetedUserProtectionAction BccMessage -EnableTargetedUserProtection $true -TargetedDomainActionRecipients test@test.nl -TargetedUserActionRecipients test@test.nl
New-AntiPhishRule -Name “Monitor Policy Phishing Rule” -AntiPhishPolicy “Monitor Policy” -RecipientDomainIs “cloudsecuritea.onmicrosoft.com”