It was already possible to use Privileged Identity Management (PIM) to manage, control and monitor administrator roles in your organization. PIM provides time-based and approval-based role activation. PIM can be used for Azure AD, Azure and other Microsoft 365 resources. It’s possible to for example require approval to activate roles, enforce multi-factor authentication and get information when someone activates their privileged role with their justification. This and more is now possible with groups. There are certain scenario’s where you use groups for administrative purposes. When you for example use role based access controls in Defender for Endpoint. There aren’t any AD roles currently for Defender for Endpoint but you can add extra groups with their respective permissions.
Privileged Identity Management is an Azure AD Premium P2 license.
How to create privileged access groups
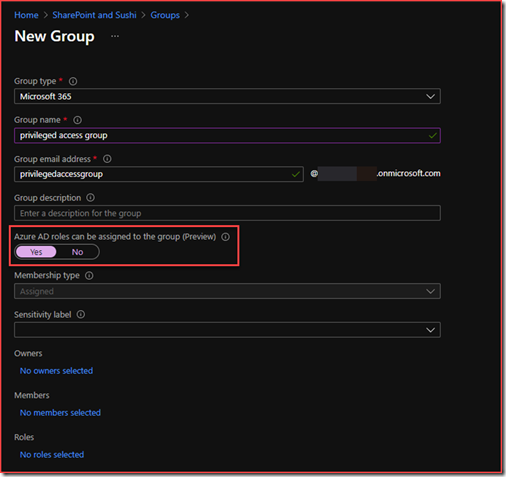
Microsoft 365 group
I’ve created a new Microsoft 365 group
Note that you need to select “Azure AD roles can be assigned to the group” in order to configure privileged access groups.
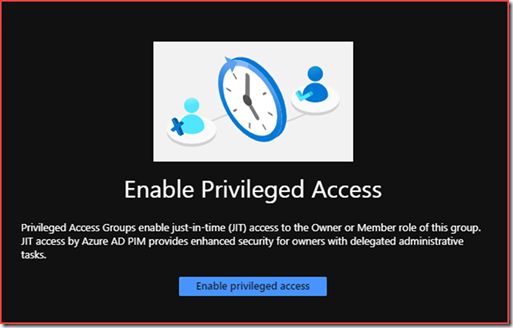
Configure privileged access
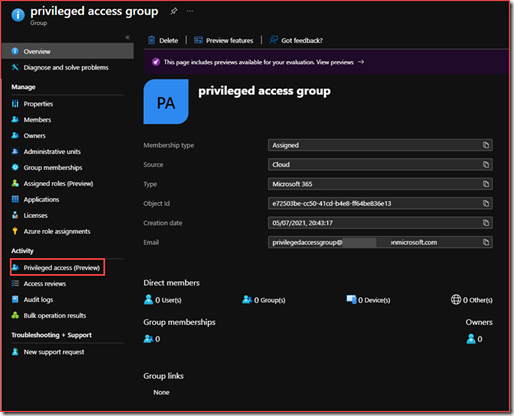
Open the newly created group
Select “Privileged access”
Enable privileged access
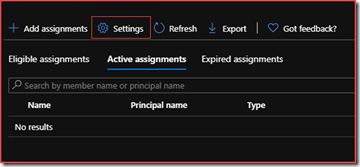
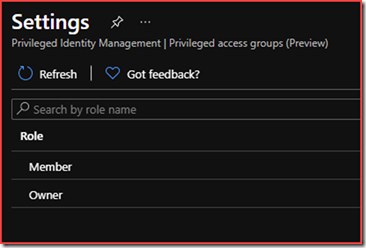
Settings
Select Member or Owner
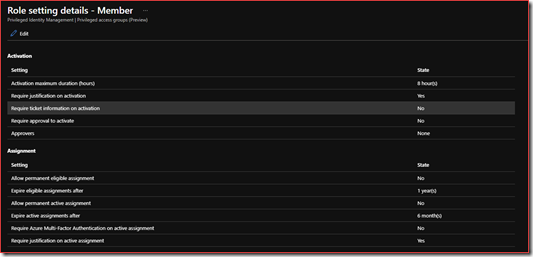
Edit the settings if needed and go back to the privileged access group settings
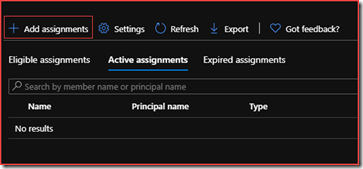
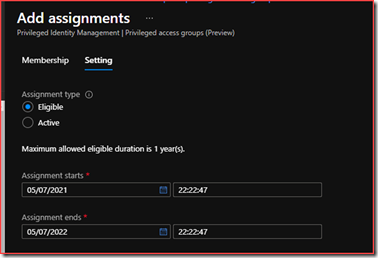
Add assignments
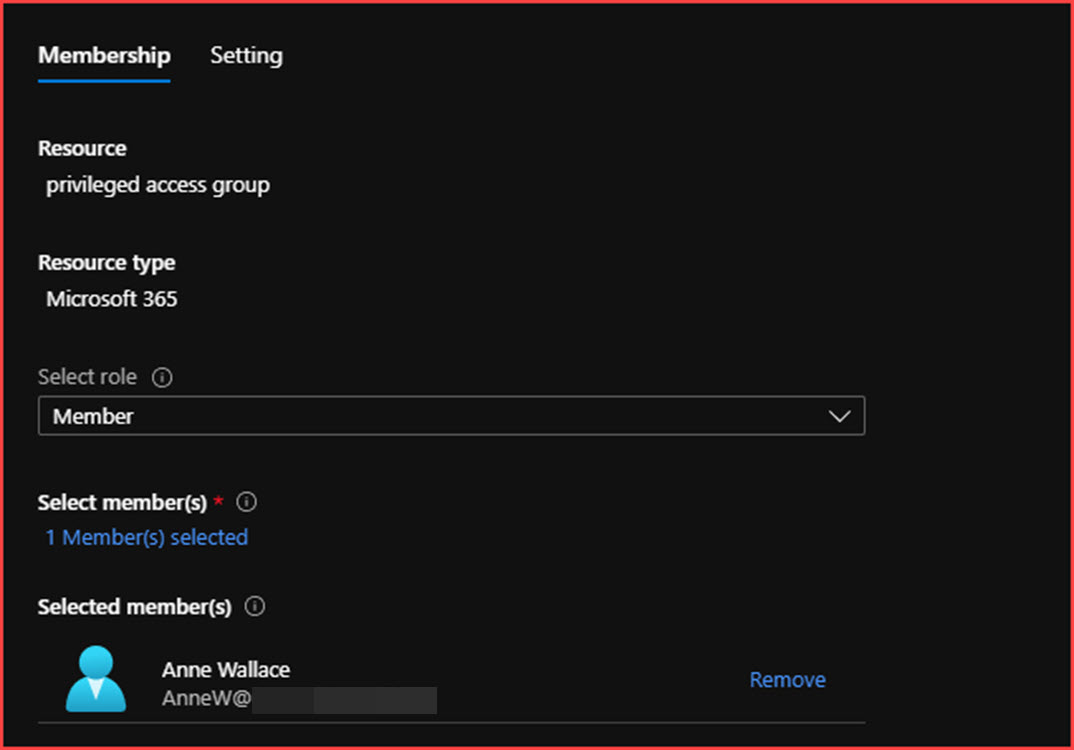
Add member and select Next
Select Eligible and click on Assign
User behaviour
Go to https://portal.azure.com
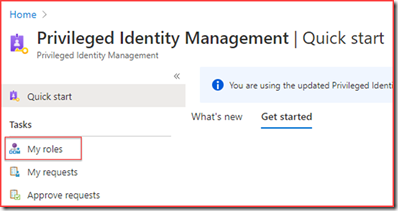
Go to Azure AD Privileged Identity Management
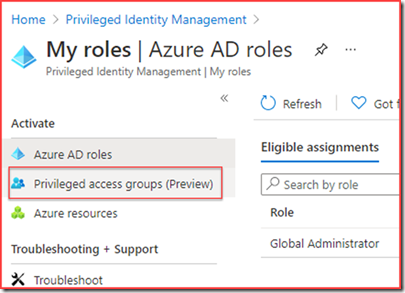
My roles
Privileged access groups
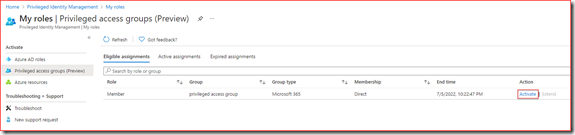
Eligible assignments and select the role for the newly created privileged access group
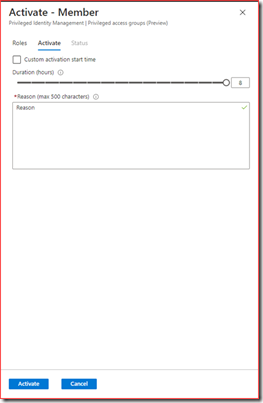
Activate
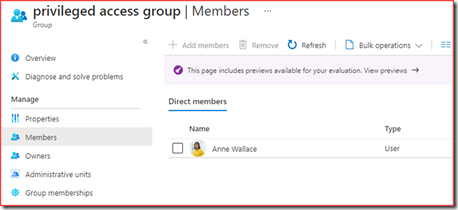
The user will be added to the group for the amount of time specified