It’s easy to manage apps when you have a clear perimeter. There is only one option to access the internet and that’s through the company firewall. Now, with people working from home and bring your own (BYO) or choose your own (CYO) devices it’s difficult. You want to maintain control on company devices by monitoring and allowing or disallowing certain applications or URL’s.
This post will show how to manage apps with Defender for Endpoint and Microsoft Cloud App Security. We will be implementing policies using Intune and configuring Defender for Endpoint and MCAS with the least amount of settings to enable the integration between MCAS –> Defender for Endpoint –> Endpoint.
Note: This setup requires a Microsoft E5 license to be able to fully use MCAS and Defender for Endpoint. It’s also possible to buy seperate stand-alone licenses but I recommend the Microsoft E5 license with all the extra security benefits.
Scenario
We have Windows 10 endpoints which are enrolled in Intune. Intune is connected with Defender for Endpoint. All onboarded Windows devices are onboarded automatically to Defender for Endpoint. The goal is to block unsanctioned apps on Windows 10 devices manually and automatically.
Configuration
Intune
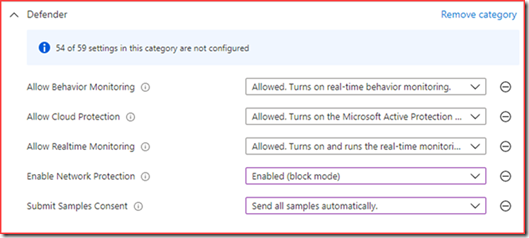
There are a few requirements from the endpoints perspective.
- Real-time protection needs to be enabled
- Cloud-delivered protection needs to be enabled
- Network protection needs to be enabled and configured to block mode
These settings can be set manually on the device, using GPO, endpoint manager or via Intune.
Note: I recommend using the Microsoft Defender for Endpoint Baseline as this includes the above requirements and more.
Create a new Windows 10 and later configuration profile using the settings catalog profile type.
Enable the above options.
Defender for Endpoint
Two features need to be enabled in Defender for Endpoint:
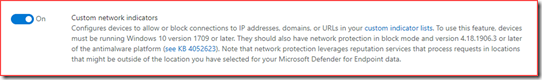
Custom network indicators
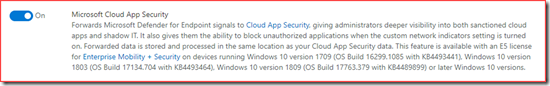
Microsoft Cloud App Security
Microsoft Cloud App Security
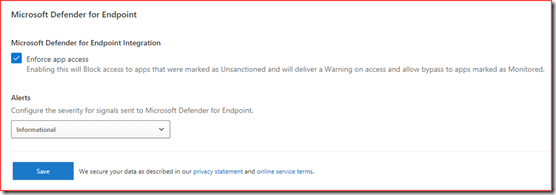
Enable “Enforce app access” on the settings page in MCAS.
Block unsanctioned apps
Manually
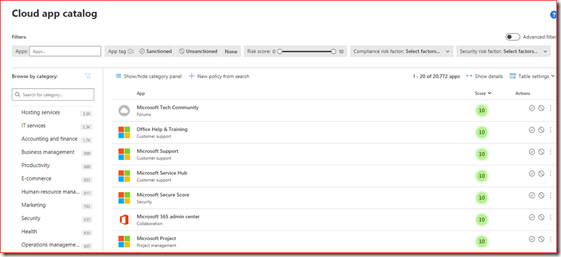
It’s possible to block apps that are being used or apps from the cloud app catalog. There are currently more than 20k apps in the cloud app catalog and it’s impossible to go through them manually.
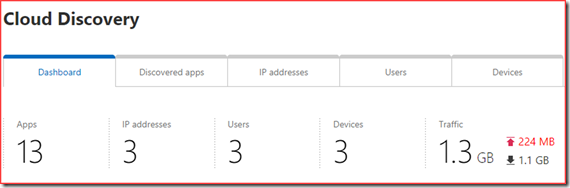
Apps that users are currently using are displayed in the cloud discovery dashboard
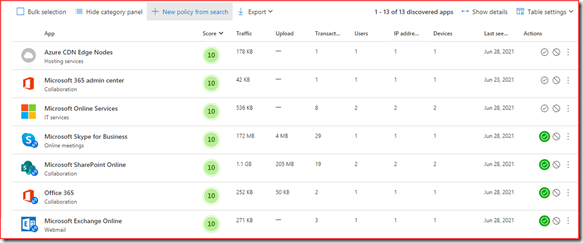
Clicking on Apps will get you to all the apps currently being used.
You can block an app by marking it as unsanctioned
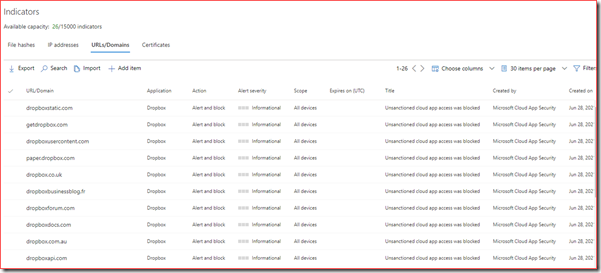
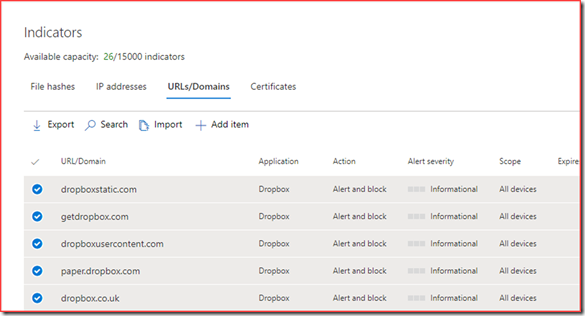
All URL’s related to Dropbox will be added to the Indicators section at Defender for Endpoint
Automatically
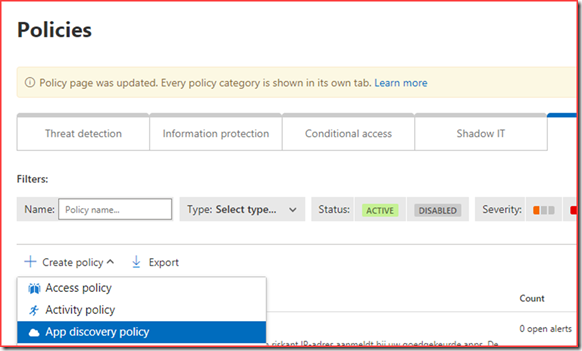
Create a new “App discovery policy” under control –> Policies
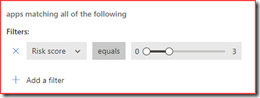
Give the policy a name and select a suitable filter
For example:
- Block apps with a risk score of 0-3
- Block apps with cloud storage as category
- Block apps with Social Network as category
- Block apps without a GDPR readiness statement
- Block apps where the headquarters is located in a certain location
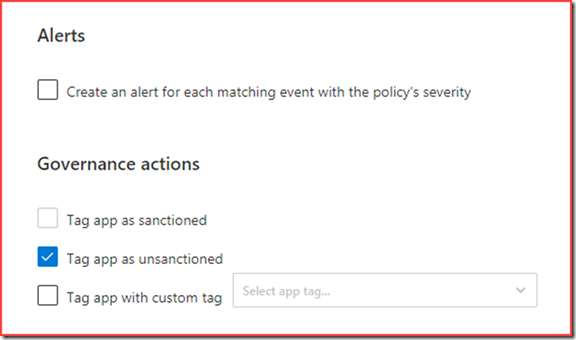
Next select that the app needs to be set as unsanctioned
User behaviour
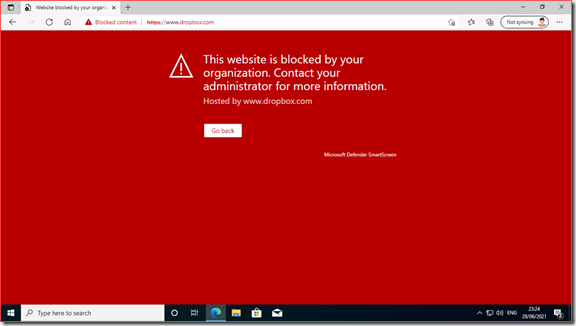
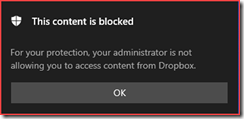
When a user tries to navigate to https://dropbox.com they will see the following screen in Edge Chromium
The app also stops working where users may receive the following message from Microsoft Defender
Additional notes
When allowing the app again you may need to remove the URLs/Domains from the Indicator list in Defender for Endpoint.