Tamper protection protects you from unwanted changes to Microsoft Defender Antivirus. Bad actors normally want to disable the firewall or antivirus in order to install additional malware. Disabling real-time protection or behavior monitoring may lead to data loss or additional attacks. Tamper protection locks Microsoft Defender Antivirus to the baseline configuration of your organization. Bad actors can’t change settings using PowerShell, registry changes or by GPO. With this setting, malicious apps are prevented from taking actions such as:
- Disabling virus and threat protection
- Disabling real-time protection
- Turning off behavior monitoring
- Disabling antivirus (such as IOfficeAntivirus (IOAV))
- Disabling cloud-delivered protection
- Removing security intelligence updates
We were already able to set tamper protection using Microsoft Intune and Microsoft Endpoint Configuration Manager (+ Tenant Attach) but now we are also able to set this for all devices using Defender for Endpoint. Tamper protection is a feature in Windows 10, Windows Server 2019, Windows Server, version 1803 or later and Windows Server 2016. An alert will be triggered in Defender for Endpoint if a tamper alert has been detected.
Note that cloud-delivered protection needs to be enabled in order to set this setting using Defender for Endpoint.
More information at Protect security settings with tamper protection | Microsoft Docs
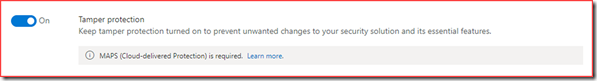
Configuration
It only requires enabling 1 feature in the Microsoft Defender Security Center.
Note that this will enable tamper protection tenant wide. You will need to use Intune or Microsoft Endpoint Configuration Manager for a more granular approach.
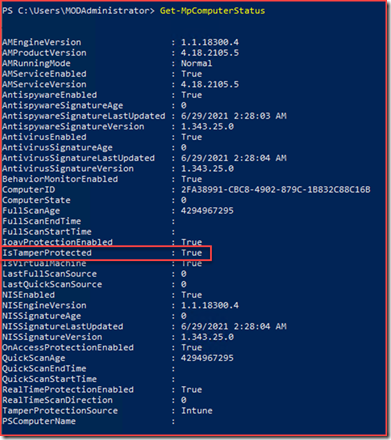
Verify it’s turned on
You can use PowerShell to verify tamper protection is enabled. Open the PowerShell app and run the Get-MpComputerStatus PowerShell cmdlet.
Test Tamper Alert
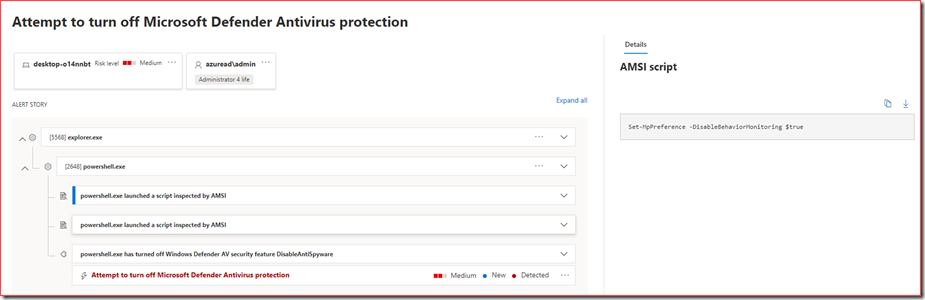
Trigger an alert by trying to turn off certain services that are related to Microsoft Defender Antivirus. The easiest way is to do this using PowerShell.
Run the following cmdlets:
- Set-MpPreference -DisableBehaviorMonitoring $true
- New-ItemProperty -Path “HKLM:\SOFTWARE\Policies\Microsoft\Windows Defender” -Name DisableAntiSpyware -Value 1 -PropertyType DWORD -Force
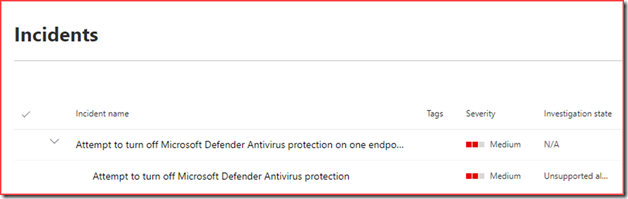
This will trigger the following incident in Defender for Endpoint