We had two cases where we encountered the error code CAA20004 with the message “AADSS90072: User account from identity provider does not exist in tenant and cannot access the application in that tenant. The account needs to be added as an external user in that tenant first.”. This blog will focus on the first case with the scenario, reason for this issue and the work around.
- The first case was with Azure Information Protection and Unified Labeling. We sent an email to different mail addresses. The recipient needed to logon with Azure Information Protection before they could open the mail. The user then received the error message in Office Outlook.
- The second case was with OneDrive for Business. OneDrive for Business was added to the users personal laptop in Word. Personal laptops are not allowed and external users cannot access these resources. The user received the same error message.
Scenario
An Office 365 user with Azure Information Protection protection sends an email to an external user.
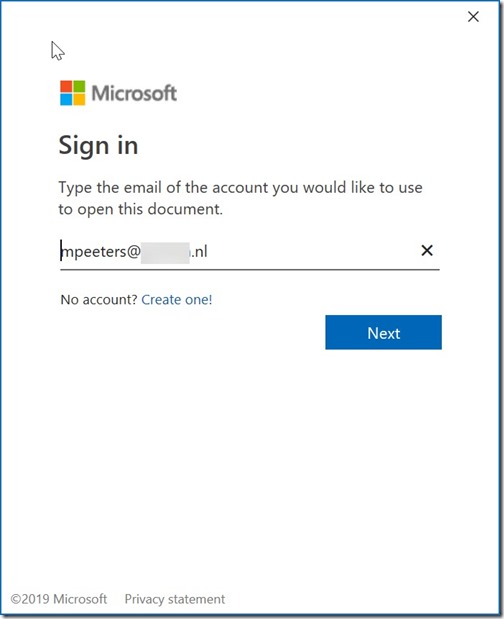
The external users receives the below email.
By opening the message the external user receives a logon prompt
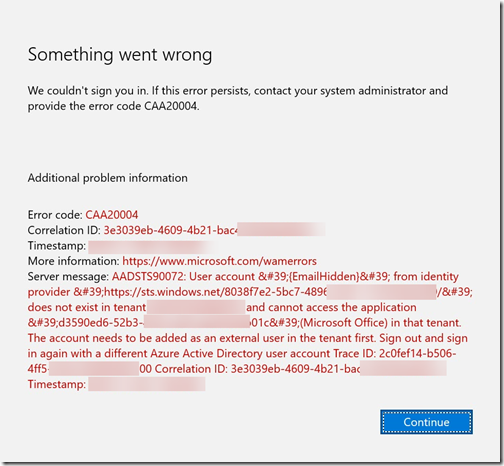
The user enters their own information and clicks on Next. The user receives the error message CAA20004 after trying to logon.
and the below after click on Continue
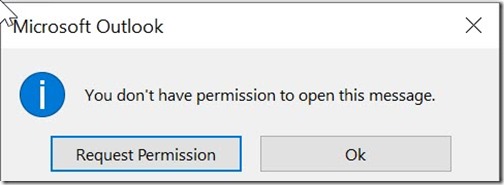
Request Permission will be sending an empty mail to the sender.
Clicking on Ok will take you to the same email where you are able to click on the link to open the mail in the browser.
Note: The default Windows 10 mail application and Outlook Web Access worked correctly. It didn’t work with Office Outlook.
Reason for this issue
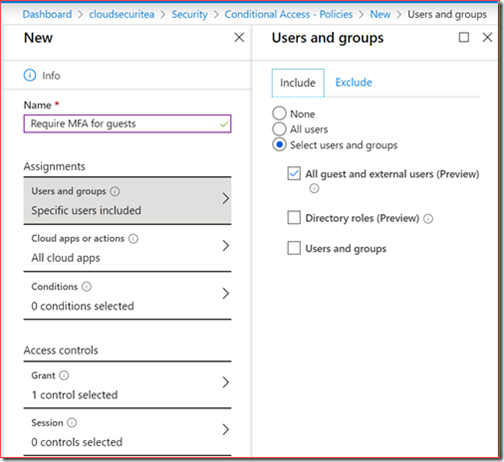
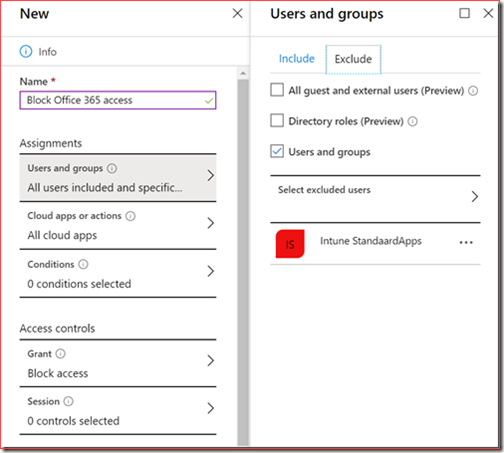
We did create and enable conditional access policies before we enabled Azure Information Protection.
One of those policies was to enable Multi-Factor Authentication for guest accounts.
All guests and external users needed to authenticate with MFA for all cloud apps.
The second policy was to restrict access to all unauthenticated users.
This just means that we created a conditional access policy for all users with an exclusion for certain groups.
The first conditional access policy is most likely the cause of this issue.
Guests are required to use MFA but also external users are required to use MFA.
External users don’t have an account in the Azure Active Directory so they can’t use MFA.
Workaround
We have discussed this case for some time with Microsoft.
In our understanding external users we sent mail to shouldn’t need to use MFA or be added as a guest account.
Microsoft’s understanding is that each external user we want to share data with AIP with should be added as a guest account.
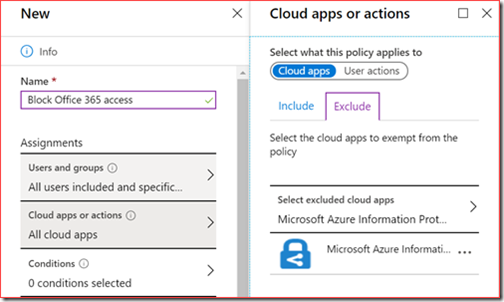
We implemented the following workaround.
We excluded the Microsoft Azure Information Protection cloud app from these policies.
Users were now able to open and read the protected mails with the correct protection applied.
The error CAA20004 was resolved but note that this is still a work around.